Why Threat Modeling is Essential for SMEs
SECURITYTHREAT MODELINGDEEPDIVESERVICEASSESSMENT
Arron 'finux' Finnon
2/5/20254 min read


Introduction
Small and medium-sized enterprises (SMEs) are increasingly reliant on technology to operate. Whether it’s managing customer data, processing payments, or running an e-commerce platform, technology plays a critical role in daily operations. Unfortunately, this reliance also makes SMEs attractive targets for cybercriminals.
The reality is stark: SMEs face unique challenges when it comes to cybersecurity. Limited budgets, minimal in-house expertise, and reliance on third-party providers leave many businesses vulnerable. Threat modeling is a proactive approach that helps SMEs stay ahead of potential cyber risks by identifying vulnerabilities before they can be exploited.
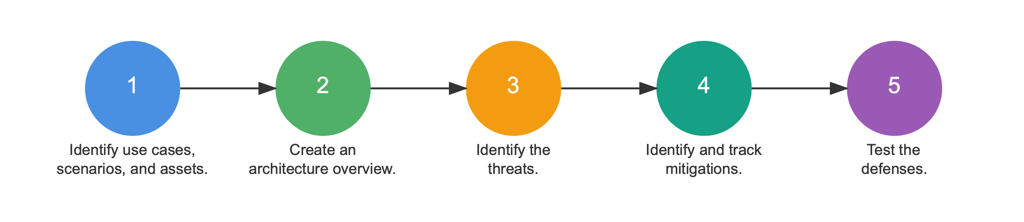
The entire process of threat modeling can be complex, but starting small is key. Here’s a simplified guide to get you going
Define the Scope: Focus on a specific system, application, or process. For example, start with how your website processes customer payments.
Identify Critical Assets: Pinpoint what needs protection—things like customer data, financial records, or intellectual property.
Spot the Threats: Consider potential vulnerabilities. Ask yourself, “How might someone try to access this data without permission?”
Assess the Impact: If this system or data were compromised, what would it mean for your business?
By breaking the process into manageable steps, you can begin building a strong foundation for cybersecurity without overcomplicating things.
Tools
To make threat modeling more accessible, here are some user-friendly tools:
Microsoft Threat Modeling Tool: A free option for creating and analyzing threat models.
Threat Dragon: An open-source tool designed for SMEs to build threat models and generate actionable reports.
These frameworks and tools simplify the process, allowing you to focus on what matters most: protecting your business.
What is Threat Modeling?
Think of threat modeling as creating a "blueprint for defense." It’s a way to identify and analyze potential threats to your systems, applications, or processes. Rather than waiting for something to go wrong, threat modeling helps you visualize how data flows through your business, pinpoint entry points for attackers, and evaluate the potential impact of a breach.
For SMEs, it’s like taking stock of your most valuable possessions, figuring out where the weak spots are, and planning how to protect them. The goal is to prepare your business to withstand cyber threats without overwhelming your resources.
Why SMEs Need Threat Modeling
Limited Resources, High Stakes
SMEs often lack the financial or technical resources of larger organizations, yet they face the same types of threats. A cyberattack could disrupt operations, damage your reputation, or even force you out of business. Threat modeling allows you to prioritize your defenses where they matter most.
Compliance Requirements
With regulations like GDPR, DORA, CRA and NIS2, protecting sensitive data isn’t just a good practice—it’s a legal requirement. Threat modeling helps SMEs map out compliance needs and reduce the risk of costly penalties.
Understanding Your Adversaries
Cyber threats come in many forms, from casual hackers to organized criminal groups. Threat modeling helps you think like an attacker, so you can anticipate and address the risks that are most relevant to your business.
How to Get Started with Threat Modeling
Threat Modeling Frameworks and Tools
Frameworks
To guide your efforts, several frameworks are available.
STRIDE: Categorizes threats into six types, including Spoofing, Tampering, and Denial of Service, helping you organize potential risks.
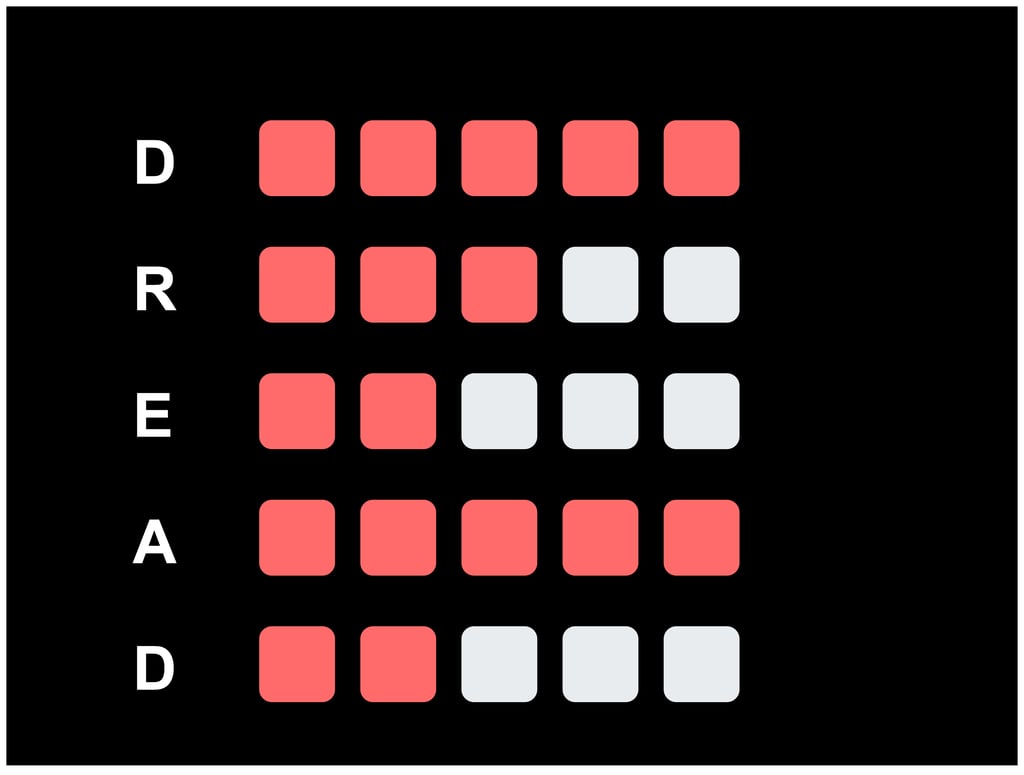
DREAD: Assesses the severity of risks based on factors like Damage Potential and Exploitability.
NIST Cybersecurity Framework: A set of best practices for managing cybersecurity risks, tailored to businesses of all sizes.
Integrating Threat Modeling with Your Security Practices
Threat modeling works best when combined with other proactive security measures.
Security Posture Reviews (SPR): These reviews help you understand your overall cybersecurity readiness and identify any gaps.
Vulnerability Assessments: Use automated scanners or manual testing to uncover known vulnerabilities and fix them before attackers exploit them.
By integrating threat modeling into your broader security strategy, you can build a more resilient defense against potential threats.
The Business Benefits of Threat Modeling
Build Stakeholder Trust
Demonstrating a commitment to cybersecurity reassures customers, partners, and investors. It shows that you’re serious about protecting their data and keeping your business safe.
Ensure Business Continuity
By addressing potential risks upfront, you can reduce downtime, prevent disruptions, and keep your operations running smoothly—even in the face of a security incident.
Make Smarter Investments
Threat modeling helps you focus your limited resources on the areas that matter most, ensuring your security budget delivers maximum value.
Conclusion
Threat modeling is an essential part of any comprehensive security strategy for SMEs. By adopting a structured approach, you can identify potential risks early, prioritize security investments, and protect your business’s most critical assets.
Protect your business today - before it’s too late.
Take the First Step Today
Threat modeling isn’t just for big corporations. SMEs can and should leverage this proactive approach to strengthen their cybersecurity defenses, meet compliance requirements, and safeguard their most critical assets.
Don’t wait for a cyberattack to disrupt your business. At SecurityWithFinux, we specialize in helping SMEs identify and mitigate potential threats. Contact us today for a free consultation and take the first step toward securing your business.
SecurityWithFinux.com
Cyber Security Solutions by
Arron 'finux' Finnon
Services
© 2025. All rights reserved.


Impressum | Privacy Policy
