Security Posture Reviews: A Deep Dive for EU SMEs
SECURITYSPRDEEPDIVEASSESSMENTSERVICE
Arron 'finux' Finnon
2/13/202510 min read


Executive Summary
Small and Medium Enterprises (SMEs) face an escalating cybersecurity crisis, with nearly 43% of cyberattacks targeting businesses with fewer than 1,000 employees. For many SMEs, a severe cyber incident can result in significant financial losses, operational disruptions, and irreparable reputational damage—often leading to business closure within months.
A Security Posture Review (SPR) serves as both a cybersecurity health check and an introduction for businesses taking their first steps toward securing their operations. By combining stakeholder interviews, asset prioritization, and actionable recommendations, an SPR helps SMEs identify vulnerabilities, implement effective controls, and build resilience against evolving cyber threats.
The Cybersecurity Landscape for EU SMEs
SMEs represent 99% of all businesses in Europe and are critical to the Digital Single Market. However, their limited resources often make them easy targets for cybercriminals. From phishing and ransomware to supply chain attacks, the threat landscape is increasingly complex. Alarmingly, only 14% of SMEs have a cybersecurity plan, while 95% of breaches involve human error. These vulnerabilities highlight the urgent need for proactive measures like SPRs.
According to a report by GetAstra, SMEs are particularly vulnerable to cyberattacks due to their lack of resources and expertise. This makes it essential for SMEs to adopt structured approaches to cybersecurity, such as SPRs, to protect their operations and comply with regulatory requirements.
https://www.getastra.com/blog/security-audit/small-business-cyber-attack-statistics/
The Role of Security Posture Reviews (SPRs)
A Security Posture Review (SPR) is a structured evaluation of an organisation's cybersecurity strategy, policies, and controls. It acts as a "health check," identifying weaknesses and providing actionable recommendations to mitigate risks. For EU SMEs, SPRs are particularly valuable in ensuring that security controls align with regulatory requirements such as GDPR and NIS2 while preparing for upcoming frameworks like the Cyber Resilience Act.
However, for many small businesses, an SPR represents much more than just an assessment—it is often their first step into thinking about cybersecurity. SMEs frequently lack the resources or expertise to develop a robust security strategy on their own. In these cases, the SPR serves as both an introduction to the concept of security and a roadmap for building a stronger cybersecurity posture over time.
Through stakeholder interviews, technical evaluations, and prioritised recommendations, an SPR helps SMEs understand their current vulnerabilities and provides them with a clear path forward. It demystifies cybersecurity by breaking it down into manageable steps, enabling even resource-constrained businesses to take meaningful action.
Important Note: While SPRs can help assess and implement security controls to meet regulatory requirements, they do not constitute legal advice. For specific legal guidance on GDPR or NIS2 compliance, consult a qualified legal professional.
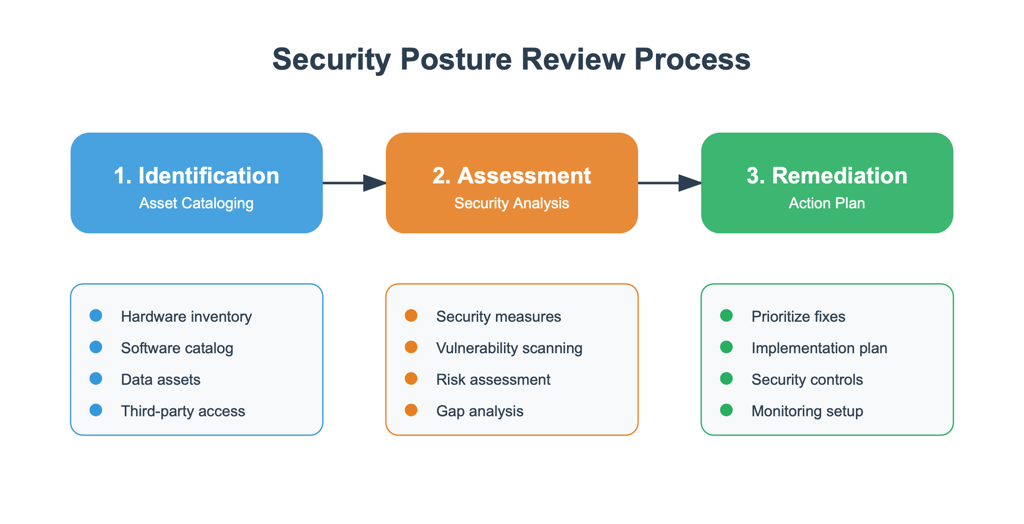
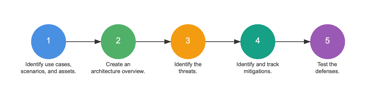
Key Components of an Effective SPR
A robust SPR leverages stakeholder interviews as a central tool to gather insights, uncover vulnerabilities, and align cybersecurity measures with business needs. These interviews, combined with technical assessments, ensure a comprehensive understanding of an organization’s security posture. The key components of an effective SPR include:
Stakeholder Interviews
Engaging with employees across all levels and departments is critical. Interviews help uncover hidden vulnerabilities, assess awareness of security practices, and identify systemic gaps in policies or processes.
These discussions provide valuable context and ensure that the review aligns with the organization’s unique operational and cultural environment.
Asset Identification and Management
Catalog all hardware, software, data assets, and third-party access points.
Prioritize critical assets based on their importance to business operations and potential impact if compromised.
Risk Assessment and Analysis
Evaluate current security policies, technical controls, and processes to identify vulnerabilities.
Ensure alignment with regulatory frameworks such as GDPR, NIS2, and other emerging EU directives.
Threat Landscape Analysis
Assess current and emerging threats specific to the SME’s industry and region.
Understand how threats could exploit identified vulnerabilities.
Security Control Evaluation
Review the effectiveness of existing security measures such as firewalls, antivirus software, access controls, and employee training programs.
Stakeholder interviews can reveal gaps in implementation or adherence to these controls.
Incident Response and Business Continuity
Analyze the organization’s ability to respond to incidents effectively while maintaining operations.
Review incident response plans, backup strategies, and disaster recovery capabilities.
Remediation Planning
Develop a prioritized action plan to address identified gaps.
Tailor recommendations based on the organization’s risk tolerance, resources, and business objectives.
By placing stakeholder interviews at the heart of the SPR process, organizations can gain deeper insights into their security posture while fostering engagement and buy-in from employees. This holistic approach ensures that technical findings are complemented by real-world operational perspectives.
Benefits of Conducting SPRs
The advantages of SPRs are universal but particularly impactful for SMEs:
Improved Security Posture: Identify and address vulnerabilities before they are exploited.
Regulatory Compliance: Align with GDPR, NIS2, and other EU directives to avoid penalties.
Cost Savings: Prevent costly incidents such as ransomware attacks or data breaches.
Employee Awareness: Foster a culture of security through training and engagement.
Business Continuity: Strengthen incident response and disaster recovery capabilities.
Case Studies:
Retail Business: A small e-commerce business identified critical weaknesses in its online platform through an SPR. By implementing stronger password policies and multi-factor authentication (MFA), they averted a potential data breach.
Manufacturing Company: A manufacturing firm strengthened its industrial control systems by implementing intrusion detection systems after an SPR revealed vulnerabilities that could disrupt production processes.
Consultancy Firm: An IT consultancy specialising in online solutions improved its resilience against ransomware by adopting immutable backups and testing restoration procedures.
EU-Specific Context
Regulatory Landscape:
GDPR: Focuses on data protection through measures like encryption, access controls, and breach notifications.
NIS2 Directive: Expands compliance obligations for essential sectors like healthcare, energy, finance, and IT services. Non-compliance can cause penalties similar to GDPR fines.
Cyber Resilience Act (CRA): Introduces cybersecurity requirements for digital products such as software and IoT devices.
While these regulations set important benchmarks for cybersecurity practices, our role is to help SMEs implement effective security controls that align with these frameworks—not provide legal advice.
Practical Tools for SMEs
For SMEs looking to take their first steps in improving their security posture, there are several free tools available that can help check for basic security best practices and configuration issues—particularly on their websites. While these tools do not replace a comprehensive SPR, they provide a useful starting point for identifying potential vulnerabilities and areas for improvement. Below is a selection of recommended tools:
securityheaders.io: Evaluates HTTP security headers on your website, such as Content Security Policy (CSP) and X-Frame-Options. These headers help protect against common vulnerabilities like cross-site scripting (XSS) and clickjacking.
ssllabs.com: Performs an in-depth analysis of your SSL/TLS configuration, checking for vulnerabilities, protocol support, and certificate issues. It assigns a grade to help you understand the strength of your website’s encryption
sitecheck.sucuri.net: Scans your site for malware, vulnerabilities, outdated software, and blacklisting status. It provides a report highlighting issues that could compromise your website’s security.
mxtoolbox.com: A versatile tool for checking and diagnosing email and DNS configurations. It allows you to look at email server configurations.
Why Use These Tools?
These tools are ideal for SMEs wanting to:
Gain quick insights into the security of their websites or systems.
Check against best practices without requiring deep technical expertise.
Identify low-hanging fruit that can be addressed quickly (e.g., enabling HTTPS or updating software).
Important Note
While these tools provide valuable insights into specific areas of security, they are not a substitute for a comprehensive SPR. An SPR goes beyond these checks by evaluating your organisation’s overall cybersecurity strategy, policies, and controls while providing a roadmap tailored to your business needs.
By combining these tools with an SPR, SMEs can take meaningful steps toward building a robust cybersecurity posture - even if they are just starting their journey into security.
Common Cyber Threats Facing SMEs
SMEs face a unique set of cybersecurity challenges, often exacerbated by limited resources, lack of in-house expertise, and a growing reliance on third-party service providers. For many SMEs, particularly those with cybersecurity skills shortages, the following threats are especially pertinent:
Phishing Attacks
Overview: Phishing remains one of the most common and effective attack methods, exploiting human error to gain access to sensitive information such as passwords or financial data.
Why SMEs Are Vulnerable: Many SMEs lack regular employee training on recognising phishing emails or messages. Attackers often target smaller businesses assuming weaker awareness and fewer technical controls.
Example: A finance employee receives an email that appears to be from their CEO requesting an urgent wire transfer. Without proper verification protocols in place, the transfer is completed before the fraud is detected.
Ransomware
Overview: Ransomware encrypts critical files, rendering them inaccessible until a ransom is paid. Some attacks now include "double extortion," where attackers threaten to leak sensitive data if payment is not made.
Why SMEs Are Vulnerable: Limited backup strategies and outdated systems make SMEs prime targets. Many smaller businesses also lack the financial and operational resilience to recover quickly from such attacks.
Example: A small healthcare clinic’s patient records are encrypted by ransomware. Without immutable backups or an incident response plan, operations are paralysed for weeks.
Supply Chain Attacks
Overview: Cybercriminals exploit vulnerabilities in an SME’s systems to infiltrate larger organisations through the supply chain.
Why SMEs Are Vulnerable: SMEs often serve as vendors or partners to larger enterprises but may lack the robust security measures required to protect shared data or systems.
Example: A small IT consultancy is compromised, allowing attackers to gain access to a major client’s network via shared credentials.
Cyber Extortion
Overview: Attackers steal sensitive data and threaten to release it unless a ransom is paid. This trend has grown significantly in sectors like professional services and manufacturing.
Why SMEs Are Vulnerable: Many SMEs underestimate the value of their data or do not have adequate protections like encryption or secure storage in place.
Example: A small law firm faces extortion after attackers steal confidential client files and threaten to leak them online.
Exploitation of Legacy Systems
Overview: Outdated software and hardware often contain known vulnerabilities that attackers can exploit.
Why SMEs Are Vulnerable: Budget constraints may prevent regular upgrades, leaving legacy systems in use far beyond their secure lifecycle.
Example: A manufacturing SME running outdated industrial control systems is targeted with malware that disrupts production processes.
Social Engineering
Overview: Attackers manipulate employees into revealing confidential information or granting access through tactics like spear phishing or pretexting.
Why SMEs Are Vulnerable: Lack of cybersecurity training leaves employees unaware of how to identify and respond to these sophisticated schemes.
Example: An attacker impersonates an IT technician over the phone, convincing an employee to provide login credentials.
Weak Password Practices
Overview: Poor password hygiene—such as using weak passwords or reusing them across multiple accounts—remains a significant risk for SMEs.
Why SMEs Are Vulnerable: Without enforced password policies or multi-factor authentication (MFA), accounts are easily compromised through brute force attacks or credential stuffing.
Example: An attacker gains access to an SME’s email system after discovering that several employees reused passwords from previously breached accounts.
Misconfigured Cloud Services
Overview: As more SMEs adopt cloud services, misconfigurations—such as leaving storage buckets publicly accessible—are becoming a common vulnerability.
Why SMEs Are Vulnerable: Limited expertise in cloud security often leads to oversight during setup and management.
Example: A public-facing database containing customer information is left exposed due to improper configuration, resulting in unauthorised access.
Checklist for Conducting an SPR
A SPR is a tailored process that evaluates an organisation's cybersecurity posture while aligning it with business priorities. For many SMEs, this is their first step into understanding and improving security. Below is a checklist based on a structured yet flexible approach:
Conduct Stakeholder Interviews
Identify key stakeholders who influence or manage critical business functions, such as those responsible for generating revenue or managing expenses.
Use open-ended questions to uncover insights about daily operations, potential risks, and existing security practices.
Focus on understanding how security impacts business-critical processes and identify gaps in awareness or controls.
Identify and Prioritise Digital and Physical Assets
Catalogue all assets (e.g., hardware, software, data, physical systems) with a focus on those critical to generating revenue or maintaining operations.
Prioritise assets based on their business criticality and potential impact if compromised.
Build a "protective wall" around high-value assets by identifying dependencies and vulnerabilities.
Review Existing Policies and Processes
Assess any existing security policies (e.g., access control policies, incident response plans) if available.
Cross-reference policies against regulatory requirements (e.g., GDPR, NIS2) and industry best practices.
Where policies are absent or inadequate, provide recommendations for creating or improving them.
Evaluate Incident Handling Capabilities
Assess how the organisation would handle a cybersecurity incident by asking scenario-based questions during stakeholder interviews.
Identify gaps in incident response planning, such as unclear roles, lack of communication protocols, or insufficient backups.
Provide guidance on developing a basic incident response plan if none exists.
Assess Employee Awareness and Training
Gauge employee understanding of cybersecurity risks through targeted interview questions.
Review any existing training programmes or awareness initiatives to identify gaps in knowledge.
Recommend practical steps to improve awareness, such as phishing simulations or regular training sessions.
Analyse Risk and Develop Remediation Plans
Work with stakeholders to identify risks based on findings from interviews and asset prioritisation.
If needed, assist in risk rating and priority mapping to help the organisation focus on addressing high-impact vulnerabilities first.
Provide a phased remediation roadmap tailored to the SME’s resources and maturity level.
Customise Recommendations Based on Scoping
Tailor the review process to align with the SME’s size, industry-specific risks, budget constraints, and security journey.
Ensure recommendations are practical and achievable within the organisation’s operational context.
Optional: Conduct Technical Assessments (if Applicable)
If the SME is further along in their security journey or requests it, perform vulnerability scans or technical assessments using appropriate tools.
Use these findings to complement insights from stakeholder interviews and policy reviews.
Call to Action
Cybersecurity is essential for protecting your business, your customers, and your reputation in today’s digital world. Whether you’re just starting to think about security or looking to strengthen your defences, a free 30-minute consultation is the perfect first step.
During this session, we’ll:
Discuss your unique business needs and challenges.
Explore how a tailored Security Posture Review (SPR) can help identify vulnerabilities and create a roadmap for improvement.
Provide actionable insights to help you start building a more secure future.
Don’t wait until it’s too late—book your consultation now! Simply visit my calendar to choose a time that suits you. Let’s work together to ensure your business is prepared for whatever comes next.
Click Here to Schedule Your Appointment

SecurityWithFinux.com
Cyber Security Solutions by
Arron 'finux' Finnon
Services
© 2025. All rights reserved.


Impressum | Privacy Policy
